RuBee Smart Weapons
A RuBee tag is embedded into the weapon. All weapons tags provide full wireless visibility on a Smart Rack, five to fifteen year battery, optional Allegro 20/20 shot counting sensors for advanced weapons maintenance.
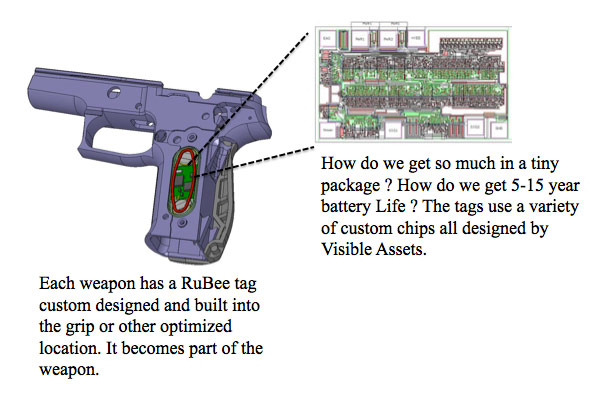
RuBee Tags Provide Real-Time Weapon Status and Visibility

- Weapons Visibility: Full weapons visibility within an area or armory physical inventory, ATF audits, as well as wireless check-in/out of weapons, and wireless weapon exit/entry detection and management. The armory visibility systems and the diagnostic data are integrated into the armory 20/20 Oracle based weapons management application that manages a RuBee network of weapons tags on Smart Racks.
- Weapons Shot Counting: Simple Rounds management functions consisting of several registers that provide tabulated total rounds fired from a weapon using an accelerometer sensor embedded in the RuBee tag.
- Mean Kinetic Shots: An optional second set of registers that tracks an advanced wear factor known as Mean Kinetic Shots (MKS) based on calculated barrel temperature, and first order and second interval statistics on total rounds fired.
- Advanced Key Performance Indicators: Real-time advanced weapon preventive diagnostics using weapon specific Key Performance Indicators (KPIs) specific and custom to the weapon. KPIs derived from the calibration described
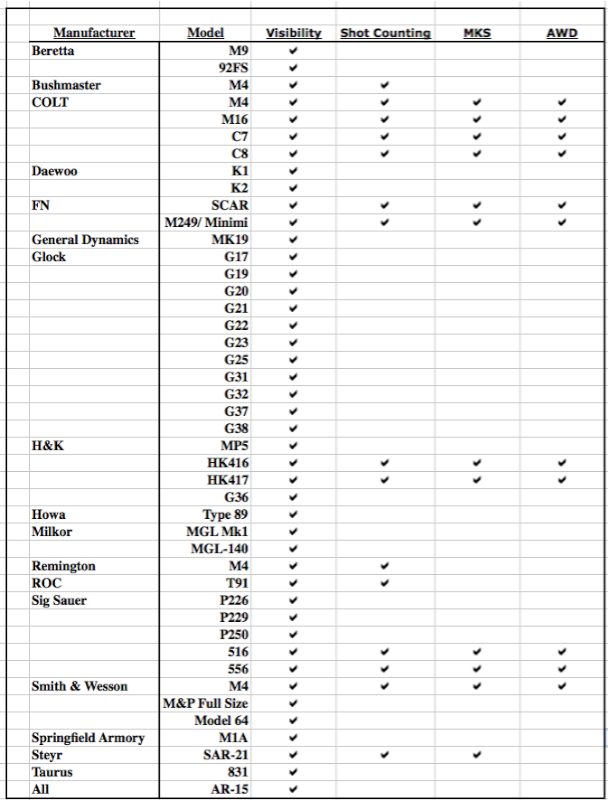
The chart below lists all current weapons supported. Maintenance features for most weapons will be added as requested.

Reading and Writing Data Stored in the Tag
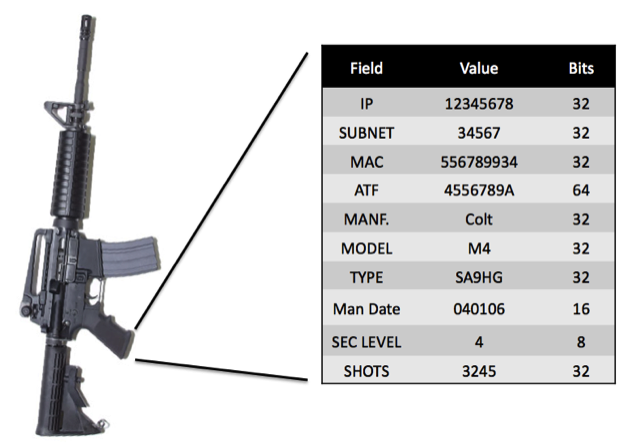
RuBee weapon tags have static memory that can be allocated to a variety of data fields. Each tag has an IP address similar to your laptop, a subnet address linked to asset class, a fixed MAC address, tied to the tag, and data tied to the weapon. The weapon data can include serial number or BATF number, manufacture date, and the manufacturer, etc. These data fields may be defined and changed by the administrative end user in armory 20/20, or with the pRap (see below).
All data once stored and defined in the tag may be automatically read and written when the weapon is placed on the Smart Rack. Reads are fully automated, and controlled by Dot-Tag and armory 20/20 application. Data may be read and written as well via tag programming features in armory 20/20. Data may also be read and written via the pRap, Visible's RuBee enabled handheld.
All data once stored and defined in the tag may be automatically read and written when the weapon is placed on the Smart Rack. Reads are fully automated, and controlled by Dot-Tag and armory 20/20 application. Data may be read and written as well via tag programming features in armory 20/20. Data may also be read and written via the pRap, Visible's RuBee enabled handheld.
Security Issues
Because the RuBee signal drops off 1/R to the 3rd power it has minimal eavesdropping risk. In contrast, RF drops off 1/R and that means it is possible to eavesdrop on RF signals many miles away from the source. RuBee signals sink into deep space noise and can not be monitored much past the tag range no matter how expensive the listening device. That provides a very high level of security with no eavesdropping risk (see Whitepaper, see Slides). RuBee also minimizes any tempest or target risks for the same reasons. In addition to the physical security layer, Visible has developed a system, called Zero Field Detectability (ZFD) that provides high tag data security in the field. Our own engineers who wrote the ZFD software can not break into, or even detect a secure tag once in the field.
